The world of cybersecurity is in constant flux, demanding that organizations continually reassess their defensive strategies. A traditional focus solely on preventing breaches, while important, is proving insufficient in the face of sophisticated and persistent threats. As highlighted in a recent Illumio podcast episode, "Trust & Resilience: The New Frontlines of Cybersecurity," the very foundation of digital interaction—trust—has ironically become a primary vulnerability exploited by attackers. This necessitates a fundamental shift in perspective.
If you're like many small and medium-sized business owners, you're juggling countless online passwords… for email, banking, software, supplier portals, and more. It's overwhelming! This often leads to using simple or repeated passwords, which unfortunately opens the door to cyber threats like data breaches, a serious risk for any business. Thankfully, there's a straightforward solution: a password manager.
Bring Your Own Device, or BYOD, is a common approach for businesses that want to take advantage of mobile technology to kickstart productivity. Instead of supplying each individual employee with company-owned devices, businesses allow employees to use their own devices for work-related purposes. While this is great on the budget, it’s only really effective (and safe) if the employee prioritizes security on their devices; otherwise, it’s a liability.
It should come as no surprise that cybersecurity is a big challenge for businesses and individuals alike. The problem: life pretty much revolves around being online these days, so there’s no avoiding it. Therefore, it’s your responsibility to ensure that any data you collect from your customers, employees, and other key stakeholders in your business is well-protected, otherwise you will face severe consequences.
We’ve all had to confirm we’re not a computer when attempting to log into an account. This is the core purpose of what once was called CAPTCHA… the Completely Automated Public Turing test to tell Computers and Humans Apart. However, it seems surprising that computers don’t easily overcome these simple-seeming tests.
Let’s dig into why these simple tests actually are effective at differentiating between human users and automated bots.
In the United States, tax season is prime time for hackers to take advantage of law-abiding, tax-paying citizens. They do this through all kinds of nefarious activities, such as phishing attacks conducted through text messages and emails claiming to be from the Internal Revenue Service. If you want to avoid getting scammed this tax season, be sure to keep the following tips in mind to stay safe while you conduct your typical tax routines.
Despite some of the headlines that we saw last year, it wasn’t all bad news regarding ransomware. Critically, 2024 saw ransomware payments plummet by hundreds of millions of dollars… despite many large-scale attacks and one record-breaking whaling payment of $75 million by one victim.
This is undeniably great to hear… but with that in mind, we cannot let ourselves slip into complacency.
Running a business is already confusing enough without worrying about security at all times. Whether you’re a small business owner or a multi-level enterprise, security is just as important for all the same reasons. Today, we want to share a couple of security strategies you can implement today to feel better about the current state of your infrastructure moving forward.
Phishing is the most common way hackers “get you,” so /to speak, but have you ever wondered why it’s so effective? Today, we want to explore the reasons why phishing schemes are so enticing to even the most security-conscious individuals out there. You might be surprised to know that even security professionals can fall prey to these types of attacks, and for very good reasons.
At the beginning of this year, a massive data breach struck a location data broker called Gravy Analytics and took possession of a dataset with 30 million points from devices worldwide. This data could potentially be used to track individuals and their movements, tellingly, through healthcare, government, and military facilities.
Unfortunately, nothing can be done about data that has already been breached, but preventative steps can and should be taken to protect your business. Let’s discuss how to prevent your applications from tracking your movements.
Did you know that phishing is, by far, the most common security risk to your business? Just think, any of your employees could become the target of a phishing attack, and all it would take is downloading the wrong file or clicking on the wrong link to expose your organization to security threats. Today, we want to offer a refresher on the throwaway signs of a phishing attack and how to protect yourself and your team from harm.
Since so much of the world is now online, businesses and organizations interact with people online now more than ever. This means they also collect people’s information, a practice they do for various reasons. Individuals need to consider their own data privacy and how it might be affected by business practices.
How seriously does your business take data privacy? Can you back up your answer with concrete examples of what you do to prioritize that notion? Today, we face a serious threat to both individual and consumer data privacy, so we want to take the time to cover how you can make data privacy a priority in your own life.
Cybersecurity is intensely important, so a business owner would think implementing every security feature and defense would be a good idea. However, as research has shown, this can be counterproductive, as only 67% of surveyed security leaders know what led to cybersecurity incidents in their businesses over the past year.
The Disney brand has long cultivated an image of magic and wonder. However, this image has yet to materialize any magical effects in reality. For example, people still suffer from food allergies while visiting Disney’s various parks.
This makes it especially dangerous that a former Disney employee was allegedly still able to access a specialized menu-planning app and make alterations, like changing prices, adding language that Disney certainly would not approve of, switching text to the unintelligible “Wingdings” font, and worst of all… changing menu information.
In June of this year, publisher Chicken Soup for the Soul Entertainment, best known for its book series of the same name, filed for Chapter 7 and Chapter 11 bankruptcy and had many of its assets liquidated. One of these assets was the movie rental service Redbox and its eponymous scarlet rental kiosks, rendering the service defunct.
However, many kiosks remain standing outside businesses even now, which makes us wonder… what about all the data they collected while they were in use?
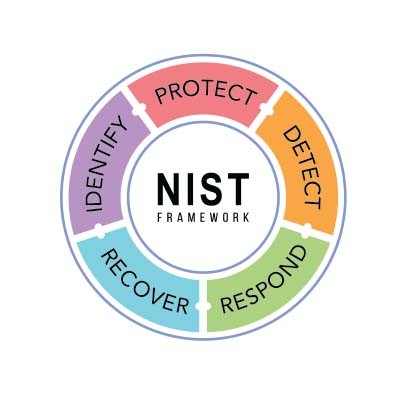
A well-structured framework is essential for establishing effective, consistent policies and strategies. This applies to many areas—including network security. Today, we’re diving into the National Institute of Standards and Technology (NIST) cybersecurity framework, which outlines steps to help safeguard your business.