How and Why Cyber Crime is so Effective
 The Internet is a fantastic tool that has ushered in an era of productivity and connectivity that we could only previously have dreamed of. Unfortunately, like every great tool, it can be used for darker, malicious purposes. In the Internet’s case, it’s used for anonymous illegal activity, like drug trafficking or selling data on the black market.
The Internet is a fantastic tool that has ushered in an era of productivity and connectivity that we could only previously have dreamed of. Unfortunately, like every great tool, it can be used for darker, malicious purposes. In the Internet’s case, it’s used for anonymous illegal activity, like drug trafficking or selling data on the black market.
There are several reasons why crime can flourish on the Internet, but the major contributor is by far the anonymity that the web offers. In particular, the anonymity browser Tor offers criminals the means to go about their duties in a way which has the least chance of being compromised by law enforcement. These black markets are often only capable of being accessed through Tor, for fear of being discovered and taken down.
However, not all online black markets are protected like this, and not all illegal online black markets prioritize sustainability. There are many underground black markets in North America that will sell to anyone, regardless of whether or not they’re seasoned criminals. This blatant disregard for their own continuity is dangerous for both its users and those orchestrating the sales. Many of these underground black market sites can be found on what’s called the “Surface Web,” which is the Internet that is seen by the average user, and is accessible to anyone. Users can access these sites by knowing what to search for, and this ease-of-use allows the industry to grow exorbitantly.
From Trend Micro via TechRepublic, here’s a chart detailing what the online crime market is primarily used for.
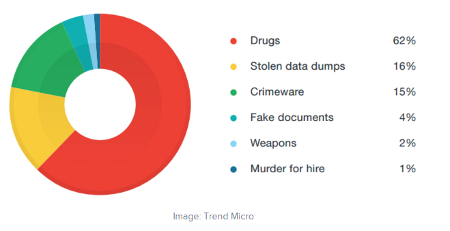
As expected, drugs are a major component of the online cybercrime industry, with stolen data dumps and crimeware coming in second and third. What’s most disturbing is that there are online plots for arms manufacturing and even assassinations, which makes the online black market an exceptionally dangerous entity.
The common consensus is that the North American underground can be considered a “glass tank.” It works great for its intended purpose, but the transparency and lack of sustainability make it susceptible to shattering at any given moment. Trend Micro reports that the life cycle of most black market sites is very short. The sites could be available one moment, and gone the next.
The lesson to be learned here is that cyber criminals are extremely resourceful and slippery, and will use any and all means at their disposal to turn a profit without a second thought. This is why it’s so challenging to protect your business from hackers and other online threats. Especially considering how anyone can purchase code over the Internet to exploit vulnerabilities, data dumps, and other sensitive credentials, business owners need to realize that there’s a market for their sensitive data, and that it needs to be protected at all costs.
Techworks Consulting, Inc. can help your business handle these threats by outfitting your network with the latest and greatest security solutions on the market. Our technicians can answer any questions you might have about firewalls, antiviruses, content blocking, and spam filtering solutions that are necessary for the average SMB. To learn more, give us a call at (631) 285-1527.


Comments